This short guide shows some important commands for your daily work on the Linux command line.
arch
Outputs the processor architecture.
$ arch
i686
cat
Outputs the contents of a file.
$ cat lorem.txt
Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
cd
Change the working directory.
$ cd /bin
chgrp
Change group ownership of files.
$ chgrp games moo.txt
chmod
Change access permissions of files.
$ chmod +x helloworld
chown
Change file owner and group.
# chown root lorem.txt
cksum
Print CRC checksum and byte counts of each file.
$ cksum lorem.txt moo.txt
3570240675 453 lorem.txt
4294967295 0 moo.txt
cp
Copies a file.
$ cp lorem.txt copy_of_lorem.txt
date
Outputs the current date and time.
$ date
Sat Mar 3 12:07:09 GMT 2007
df
Reports the amount of disk space used and available on filesystems.
$ df
Filesystem 1K-blocks Used Available Use% Mounted on<br>
/dev/simfs 39845888 218048 39627840 1% /
dir
List directory contents.
$ dir
copy_of_lorem.txt lorem.txt moo.txt www
du
Estimate file space usage.
$ du -h /bin
7.8M /bin
echo
Display a line of text.
$ echo foobar
foobar
exit
Cause the shell to exit.
$ exit
fgrep
Print lines matching a pattern in a file.
$ fgrep "irure dolor" lorem.txt
commodo consequat. Duis aute irure dolor in reprehenderit in voluptate
find
Search for files in a directory hierarchy.
$ find hello*
hello_world
hello_world.c
free
Display amount of free and used memory in the system.
$ free
total used free shared buffers cached
Mem: 8299892 8287708 12184 0 2641772 1731236
Low: 3581300 3572764 8536
High: 4718592 4714944 3648
-/+ buffers/cache: 3914700 4385192
Swap: 8193140 2335664 5857476
grep
Print lines matching a pattern.
$ grep -i apple fruitlist.txt
apple
groups
Outputs the user groups of which your account belongs to.
$ groups
games users
head
Output the first part of files.
$ head -2 lorem.txt
Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod
tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim
hostname
Outputs the machines hostname on the network.
$ hostname
anapnea.net
id
Outputs user id, group id, and groups of your account.
$ id
uid=1478(smallfoot) gid=100(users) groups=35(games),100(users)
kill
End a process.
$ kill -9 18298
-bash: kill: (18298) - Operation not permitted
killall
Kill processes by name.
$ killall irssi
irssi(18298): Operation not permitted
irssi(13372): Operation not permitted
irssi(22048): Operation not permitted
irssi: no process killed
last
Show listing of last logged in users.
$ last -n 3
alice pts/6 192.0.34.166 Fri May 18 16:17 still logged in
bob pts/2 64.233.183.103 Fri May 18 16:17 still logged in
clare pts/6 72.5.124.61 Fri May 18 15:54 - 15:55 (00:01)
ldd
Print shared library dependencies.
$ ldd /bin/bash
libncurses.so.5 => /lib/libncurses.so.5 (0x40023000)
libdl.so.2 => /lib/libdl.so.2 (0x40065000)
libc.so.6 => /lib/libc.so.6 (0x40069000)
/lib/ld-linux.so.2 (0x40000000)
ln
Make links between files.
$ ln -s data.txt symlink.txt
logname
Print user's login name.
$ logname
smallfoot
ls
List directory contents.
$ ls
copy_of_lorem.txt lorem.txt moo.txt www
man
Opens the manual page for a software or function.
$ man bash
md5sum
Outputs the MD5 hash sum of a file.
$ md5sum lorem.txt
56da9e37259af34345895883e6fd1a27 lorem.txt
mkdir
Makes a directory.
$ mkdir foobar
mv
Moves a file.
$ mv lorem.txt ipsum.txt
nl
Number lines of files.
$ nl lorem.txt
1 Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod
2 tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim
3 veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea
4 commodo consequat. Duis aute irure dolor in reprehenderit in voluptate
5 velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint
6 occaecat cupidatat non proident, sunt in culpa qui officia deserunt
7 mollit anim id est laborum.
nm
List symbols from object files.
$ nm hello_world
080494a0 D _DYNAMIC
0804956c D _GLOBAL_OFFSET_TABLE_
08048474 R _IO_stdin_used
w _Jv_RegisterClasses
08049490 d __CTOR_END__
0804948c d __CTOR_LIST__
08049498 d __DTOR_END__
...
od
Dump files in octal and other formats.
$ od -t x /bin/sh
2376640 00098020 000054d4 00000000 00000000
2376660 00000020 00000000 000000c7 00000008
2376700 00000003 080e6500 0009d4f4 00004ae8
...
pidof
Find the process ID of a running program.
$ pidof fetchmail
22392
ping
Pings a host.
$ ping -c 2 127.0.0.1
PING 127.0.0.1 (127.0.0.1) 56(84) bytes of data.
64 bytes from 127.0.0.1: icmp_seq=1 ttl=64 time=0.048 ms
64 bytes from 127.0.0.1: icmp_seq=2 ttl=64 time=0.052 ms
--- 127.0.0.1 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 999ms
rtt min/avg/max/mdev = 0.048/0.050/0.052/0.002 ms
ps
Outputs running processes.
$ ps
PID TTY TIME CMD
21542 pts/12 00:00:00 bash
27706 pts/12 00:00:00 ps
pstree
Display a tree of processes.
$ pstree
init-+-2*[BitchX]
|-3*[bash---sleep]
|-fetchmail
|-screen-+-bash---irssi
| `-bash---ctorrent
|-screen-+-bash---lisp.run
| |-bash---vi
| |-2*[bash]
| `-bash---lynx
|-2*[screen---bash---irssi]
|-screen---irssi
|-screen---bash
|-screen-+-bash
| `-irssi
|-skjerm---irssi
|-sshd-+-5*[sshd---sshd---bash---irssi]
| |-8*[sshd---sshd---bash]
| |-sshd---sshd---bash---screen
| |-sshd---sshd
| `-sshd---sshd---bash---pstree
`-syslog-ng
pwd
Outputs the name of current working directory.
$ pwd
/home/smallfoot
rm
Removes a file or directory.
$ rm lorem.txt
rmdir
Removes a directory.
$ rmdir foobar
sed
Stream editor for filtering and transforming text.
$ echo "My cat's name is Bob" | sed -e 's/Bob/Mittens/g'
My cat's name is Mittens
sha1sum
Outputs the SHA1 hash sum of a file.
$ sha1sum lorem.txt
c942ddebd142ec8bacac9213d48096e74bab4957 lorem.txt
shutdown
Bring the system down in a secure way. All logged-in users are notified that the system is going down.
$ shutdown now
size
List section sizes and total size.
$ size /bin/bash
text data bss dec hex filename
621233 22712 19176 663121 a1e51 /bin/bash
stat
Outputs file status.
$ stat lorem.txt
File: `lorem.txt'
Size: 453 Blocks: 8 IO Block: 4096 regular file
Device: 77h/119d Inode: 27312217 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1478/smallfoot) Gid: ( 100/ users)
Access: 2007-03-03 12:24:39.000000000 +0000
Modify: 2007-03-03 12:24:39.000000000 +0000
Change: 2007-03-03 12:24:39.000000000 +0000
strings
Print the strings of printable characters in files.
$ strings hello_world
/lib/ld-linux.so.2
_Jv_RegisterClasses
__gmon_start__
libc.so.6
puts
_IO_stdin_used
__libc_start_main
GLIBC_2.0
PTRh%
[^_]
Hello World!
tail
Output the last part of files.
$ tail -2 lorem.txt
occaecat cupidatat non proident, sunt in culpa qui officia deserunt
mollit anim id est laborum.
talk
Talk to another user.
$ talk bob Lookout for the dopefish!
touch
Change a file's access and modification timestamps. If file does not exist, create it.
$ touch lorem.txt
tty
Outputs the name of the current terminal.
$ tty
/dev/pts/16
uname
Outputs operating system, hostname, kernel version, date and timp, and processor.
$ uname -a
Linux anapnea.net 2.6.9 #1 SMP Wed Jul 19 16:24:18 MSD 2006 i686 Intel(R) Xeon(TM) CPU 2.80GHz GenuineIntel GNU/Linux
uptime
Outputs the system uptime.
$ uptime
14:50:26 up 7 days, 17:52, 18 users, load average: 0.08, 0.02, 0.01
users
Print the user names of users currently logged in to the current host.
$ users
alice bob charlie eve
vdir
List directory contents.
$ vdir
total 8
-rw-r--r-- 1 smallfoot users 453 Mar 3 12:32 copy_of_lorem.txt
-rw-r--r-- 1 smallfoot users 453 Mar 3 12:24 lorem.txt
-rw-r--r-- 1 smallfoot users 0 Mar 3 12:32 moo.txt
lrwxr-xr-x 1 root root 18 Feb 27 19:33 www -> /var/www/smallfoot
w
Show who is logged on and what they are doing.
$ w
12:14:30 up 5 days, 15:16, 19 users, load average: 0.00, 0.00, 0.00
USER TTY LOGIN@ IDLE JCPU PCPU WHAT
charlie pts/0 Fri21 3:26m 2.52s 2.52s irssi
alice pts/2 Wed17 30:21m 0.00s 0.00s -bash
emma pts/4 11:37 36:57 0.00s 0.00s -bash
frank pts/5 11:48 11:03 0.00s 0.00s -bash
smallfoo pts/12 12:01 0.00s 0.04s 0.01s w
wall
Send a message to everybody's terminal.
$ wall next week we change the server for a new one
wc
Counts lines in a file.
$ wc -l lorem.txt
7 lorem.txt
whatis
Search the whatis database for complete words.
$ whatis bash
bash (1) - GNU Bourne-Again SHell
bash [builtins] (1) - bash built-in commands, see bash(1)
who
Outputs who is currently logged into the system.
$ who
charlie pts/0 Mar 2 21:37 (xtreme-11-65.acme.com)
alice pts/2 Feb 28 17:48 (147.21.16.3)
emma pts/4 Mar 3 11:37 (32.84-48-181.uac.com)
frank pts/5 Mar 3 11:48 (port-212-202-233-2.foobar.org)
smallfoot pts/12 Mar 3 12:01 (c-12776f4.cust.example.net)
whereis
Locate the binary, source, and manual page files for a command.
$ whereis bash
bash: /bin/bash /etc/bash /usr/share/man/man1/bash.1.gz
whoami
Outputs your username / the name of your account.
$ whoami
smallfoot

























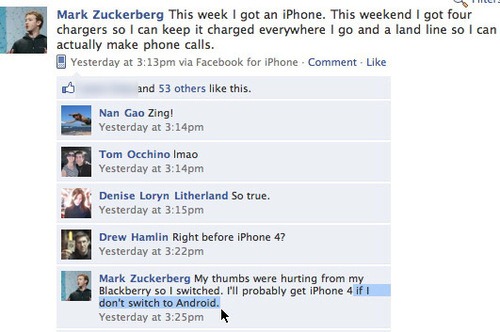 Mark Zuckerberg Profile on Facebook, June 2010
Mark Zuckerberg Profile on Facebook, June 2010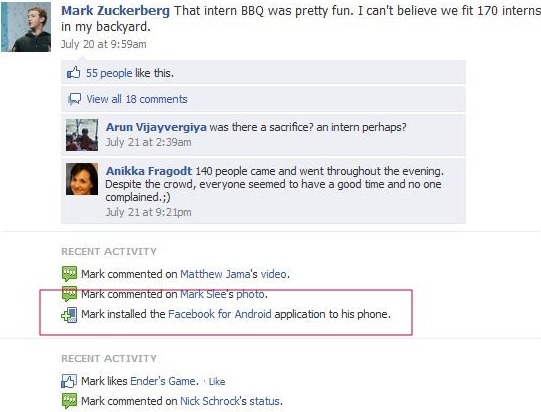 Mark Zuckerberg Profile on Facebook, July 2011
Mark Zuckerberg Profile on Facebook, July 2011





