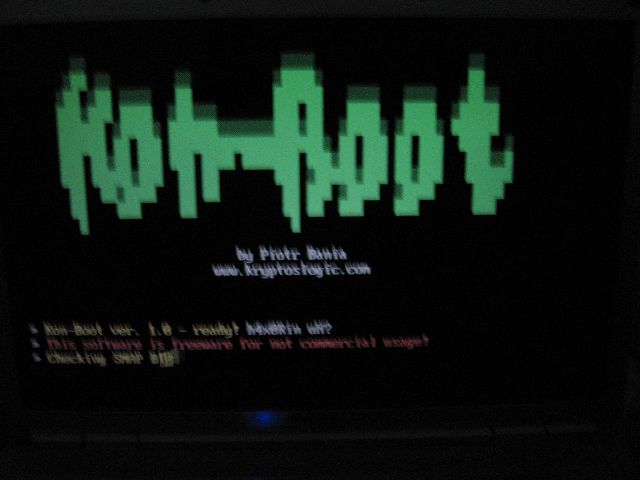
Recover Or Reset Ur Windows Pwd Using Ubuntu
Recover Or Reset Ur Windows Pwd Using Ubuntu , By h4ckfreak
Showing posts with label News. Show all posts
Showing posts with label News. Show all posts
Tuesday, December 13, 2011
Tuesday, August 9, 2011
10-year-old hacker discovers mobile game security hole

The hacker is a 10-year-old girl who goes by the name of CyFi, according to a story from PC World. She presented last weekend at DefCon Kids, a children-oriented offshoot of the annual DefCon hacker conference that took place in Las Vegas. And the exploit she found is a pretty simple one: by messing with her mobile device’s clock, she was able to alter the in-game time in her farming simulation app (read: FarmVille or a similar game), thereby shortening the time the game required her to wait for her crops to grow. The hack works on games both on Google’s Android operating system and Apple’s iOS platform.
That’s a pretty simple exploit and one that players have been trying with games pretty much since video games and computer games have been available. It’s also one that programmers have long since figured out how to stop – which is the reason you can’t mess with your computer’s clock in order to extend a free trial of software, for example. Except, as CyFi put it, app developers are still busy feeling-out how to work in the space and not quite onto thinking about security yet. Here’s a quote from the brief for CyFi’s presentation, entitled “Apps – A Traveler of Both Time and Space (And What I Learned About Zero-Days and Responsible Disclosure)”:
The world of apps has obvious[ly] not thought about security, yet. Here is an import[ant] lesson they can learn from a Girl Scout. I’ll show a new class of vulnerabilities I call TimeTraveler. By controlling time, you can do many things, such as grow pum[p]kins instantly. This technique enables endless possibilities. I’ll show you how. Wanna play a game? Let’s find some zero-days! (Cuz it’s fun!)
While CyFi presented on the exploit she’d discovered at DefCon, she wasn’t giving away the keys to the farm, as it were. The hacker kept her method secret, she said, in order to give game developers time to fix the problems. The hack has been independently verified; CyFi discovered that there are anti-cheat components worked into apps, but they’re not very robust. After some experimentation, she was able to trick them by taking her device off Wi-Fi connectivity and by moving the clock in small increments so as not to tip off the software.
That’s a pretty simple exploit and one that players have been trying with games pretty much since video games and computer games have been available. It’s also one that programmers have long since figured out how to stop – which is the reason you can’t mess with your computer’s clock in order to extend a free trial of software, for example. Except, as CyFi put it, app developers are still busy feeling-out how to work in the space and not quite onto thinking about security yet. Here’s a quote from the brief for CyFi’s presentation, entitled “Apps – A Traveler of Both Time and Space (And What I Learned About Zero-Days and Responsible Disclosure)”:
The world of apps has obvious[ly] not thought about security, yet. Here is an import[ant] lesson they can learn from a Girl Scout. I’ll show a new class of vulnerabilities I call TimeTraveler. By controlling time, you can do many things, such as grow pum[p]kins instantly. This technique enables endless possibilities. I’ll show you how. Wanna play a game? Let’s find some zero-days! (Cuz it’s fun!)
While CyFi presented on the exploit she’d discovered at DefCon, she wasn’t giving away the keys to the farm, as it were. The hacker kept her method secret, she said, in order to give game developers time to fix the problems. The hack has been independently verified; CyFi discovered that there are anti-cheat components worked into apps, but they’re not very robust. After some experimentation, she was able to trick them by taking her device off Wi-Fi connectivity and by moving the clock in small increments so as not to tip off the software.
Talks about app security inevitably seem to lean toward the spooky, but for one hacker, finding an exploit in apps wasn’t about stealing credit card information, just fast-tracking the growth of her crops.
Friday, May 13, 2011
How to Use Google Wave , Tool for Hacking
I Thought i was Fooled When Google WAVE Was released On April 1 , After a day only i Fathom that Google Wave Service Exists ..Well Coming to tha Point ,Many security researchers and hackers are familiar with BeEF, a browser exploitation framework by Wade Alcorn. In short, BeEF is a program that brings together various types of code for taking advantage of known vulnerabilities in web browsers. If a target computer loads a certain bit of code within a web page, that code connects to a server control panel which can then execute certain attacks against the “zombie” machine.
After noting potential security issues with the gadgets in Google Wave, I set about to finally setup a BeEF testbed and see if Google Wave was as capable a platform for malware delivery.
The picture above shows the results. I successfully created a Google Wave gadget that creates a new BeEF zombie whenever someone views the wave. This does not allow for the keylogger function of BeEF, but I did send an alert dialog (as shown) and used the Chrome DoS function to crash the browser tab. (I could also detect that the zombie machine had Flash installed – imagine the possibilities of using Flash or PDF exploits in an auto-loaded gadget.)
What’s even more disconcerting is that BeEF can integrate with Metasploit to potentially take over a victim’s machine. I do not currently have Metasploit setup to test using Autopwn, but based on my experiences so far, I’m fairly confident such an attack would succeed.
All of these demonstrations about security and Google Wave point to four general weaknesses in Wave’s current structure:
After noting potential security issues with the gadgets in Google Wave, I set about to finally setup a BeEF testbed and see if Google Wave was as capable a platform for malware delivery.
Example of a BeEF zombie spawned via Google Wave
What’s even more disconcerting is that BeEF can integrate with Metasploit to potentially take over a victim’s machine. I do not currently have Metasploit setup to test using Autopwn, but based on my experiences so far, I’m fairly confident such an attack would succeed.
All of these demonstrations about security and Google Wave point to four general weaknesses in Wave’s current structure:
- Allowing scripts and iframes in gadgets with no limits apart from sandboxing
- Lack of control over what content or users can be added to a wave
- No simple mechanism for verifying gadget sources or features
- Automatically loading gadgets when a wave is viewed
Friday, January 7, 2011
PandaLabs Annual Report 2010
In 2010, cyber-criminals have created and distributed a third of all existing viruses. That is, in just 12 months, they have created 34 percent of all malware that has ever existed and has been classified by the company. Furthermore, the Collective Intelligence system, which automatically detects, analyzes and classifies 99.4 percent of all malware received, currently stores 134 million unique files, out of which 60 million are malware (viruses, worms, Trojans and other computer threats).
Topics covered:
* Threats in 2010
* Stuxnet, Iran and nuclear plants
* Cyber war
* Aurora
* Cyber-crime
* Cyber-protests
* Mariposa
* Social networks
* Rogueware
* 2010 in figures
* More BlackHat SEO
* Windows 7 vs Mac OS X Snow Leopard
* Cell phone security
* Spam in 2010
* Vulnerabilities in 2010
* Trends in 2011
* Conclusion
Trojans still dominate the ranking of new malware that has appeared in 2010 (56 percent of all samples), followed by viruses and worms. It is interesting to note that 11.6 percent of all the malware gathered in the Collective Intelligence database is rogueware or fake antivirus software, a malware category that despite appearing only four years ago is creating much havoc among users.
Click here to read full report
Topics covered:
* Threats in 2010
* Stuxnet, Iran and nuclear plants
* Cyber war
* Aurora
* Cyber-crime
* Cyber-protests
* Mariposa
* Social networks
* Rogueware
* 2010 in figures
* More BlackHat SEO
* Windows 7 vs Mac OS X Snow Leopard
* Cell phone security
* Spam in 2010
* Vulnerabilities in 2010
* Trends in 2011
* Conclusion
Trojans still dominate the ranking of new malware that has appeared in 2010 (56 percent of all samples), followed by viruses and worms. It is interesting to note that 11.6 percent of all the malware gathered in the Collective Intelligence database is rogueware or fake antivirus software, a malware category that despite appearing only four years ago is creating much havoc among users.
Click here to read full report