I initiated a thread in my facebook defend hackers group for seeking a help to resolve my issue:
I was using a ADSL broadband connection from India's largest ISP - BSNL. I was using an ancient modem/router to connect to Internet - Pronet PN-ADSL 101E/U:
As you can see below it has only one RJ45 out. So I was able to connect only one PC at a time. And currently I have two desktops and a laptop. So it was really headache to wait till my dad or brother accessing Internet on other PC.
So I decided to buy a new one. I went for a ADSL-less wireless router, since I wanted to ensure that the new one will work with cable net too (in case I change my ISP). So I bought TP-LINK wireless router: TL-WR941ND on Flipkart:
I configured my ADSL modem/router in bridge through its management console
To open management console of any router, you have to connect to it through wire. You cannot configure router when you are connected wirelessly.
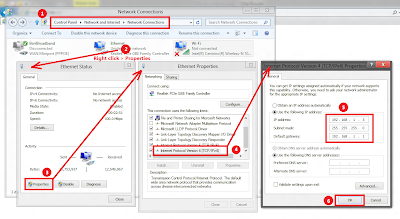
Management console of old modem/routers usually opens up when you put http://192.168.1.1/ in the browser's address bar. If it doesnt open up, you may need to change the IP address of your NIC to something 192.168.1.5 (the last number can be anything but not 1), subnet mask to 255.255.255.0 and the default gateway to 192.169.1.1:
For new routers the address for management console may be different (You can also try 192.168.0.1). Usually you can find the default domain name in the router's manual. This domain name can be put in the browser's address bar instead of IP address. For example my new routers user guide says that default domain name is http://tplinklogin.net, the default IP address is 192.168.0.1.
When you put appropriate address, it asks for username and password which is usually admin and admin for most routers (check manual if it does not work ).
The bridging option can be done in management console. Generally the option shows in the Advanced Network Setup option. ( However different routers have different management console layout, so just check the manual ):
Then I setup router in following way:
Connecting the output of my old router to input WAN RJ45 of new router and then connecting my PC to anyone of the LAN ports of new router. Then I configured the new router in PPPoE through its management console and entered the username and password so that my new router will automatically login to the connection from my old router:
Oh yes, if you have changed your PC's IP address using procedure above while trying to open up your router's management console, change it to "Obtain an IP address automatically" (thats what usually ISPs do, but you may need to check with your ISP):
With that done I was able to connect my new router both through wire and wirelessly, but then there was a problem - it is not allowing access to some sites. Most notably yahoo.com (though ymail was working ), msn.com and yeah microsoft.com toooo. So that was seriously unacceptable. I did quick google and got some suggestions like adding rules to router to allow some ports. I did many of them but none worked. After hours of search I read something about Maximum Transfer Unit (MTU):
MTU of a communications protocol of a layer is the size (in bytes) of the largest protocol data unit that the layer can pass onwards. If the MTU size set in your router exceeds that can be handled by the devices at the backbone or by your ISP, then it may lead to packet retransmissions or eventually some sites getting blocked (at the router which cannot handle the bigger MTU sizes). Too small size may lead to excessive fragmentation, header overhead and acknowledgements.
Some sites went on saying:
The usual minimum MTU size for dial-ups is 576. So, with MTU = 576, possibility that the problem is solved is more. So change the MTU size to 576 and then go on increasing it by ten while checking whether connection works or not. The optimal MTU size will be the maximum one where router shows up all the websites.
Changing MTU to 576 surprisingly worked for me, but then I went to check out what will be the optimal MTU size. So the obvious idea was to check the MTU of the old router. First I connected my PC back directly to the old router. But the old routers' management console was so dumb that it did not showed anything called MTU (forget about changing MTU size). So I went on checking the other ways to check MTU size for the old router. And fortunately I found some DOS commands. This one really worked for me:
C:\Users\suren>netsh interface ipv4 show subinterfaces
I realized that the MTU size for my connection was 1460:
So I just went to the management console of new router (of course I connected my routers back in the setup showed above) and changed the MTU size from the default of 1480 to 1460:
And finally things started all working. That difference of 20 bytes was making all the mess!!! Now I can access all sites and yes microsoft.com too!!!!
And finally things started all working. That difference of 20 bytes was making all the mess!!! Now I can access all sites and yes microsoft.com too!!!!